An Optus data breach shook far more people than many first expected.It wasn’t because the whole idea of a data breach was new, but due to the nature of the information leaked and the fact the whole thing was kept so quiet. Names, dates of birth, phone numbers, ID details. Things you don’t just change and forget. Even now, long after the first headlines faded, people are still dealing with the consequences in small, ongoing ways.
Optus data breach is a significant cybersecurity incident that was compromised personal data of millions of customers in Australia. The breach raised serious issues concerning data security, privacy laws, and the responsibility of corporations. Furthermore, besides the technical failure, the breach resulted in lawsuits, class actions, and the issue of trust that has not been completely resolved until now.
What is the Optus data breach?
It was a massive exposure of people’s personal data of customers when a compromised party accessed Optus systems without authorization in 2022.
Is the Optus data breach still relevant?
Legal cases, discussions about the compensation, and privacy reforms are still unfolding.
How did the Optus data breach happen?
Optus said that the breach had taken place via an exposed API that gave access to the system without proper authentication.
How the Optus Data Breach Worked
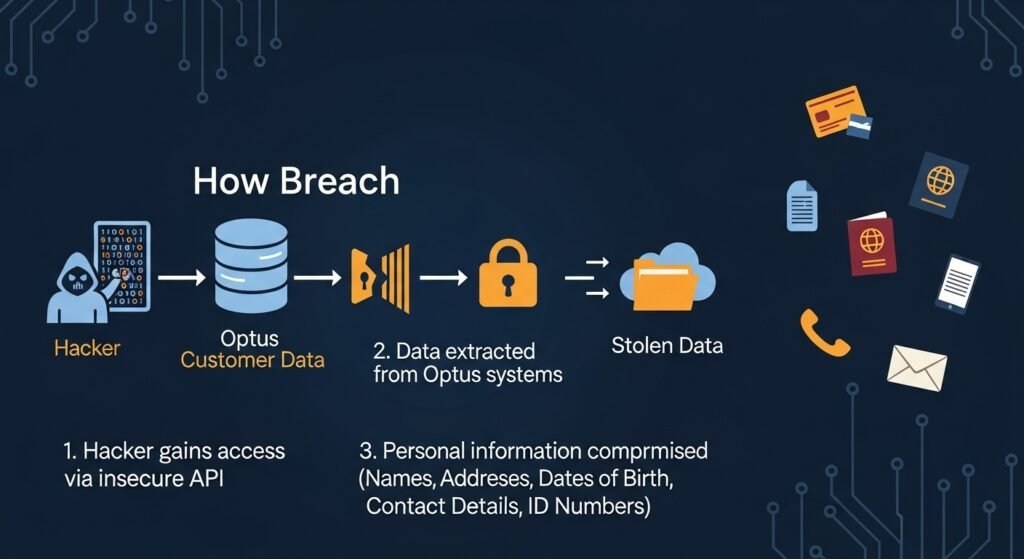
From the technical standpoint, the breach didn’t occur due to viruses or accessing accounts through stolen passwords. This was one of the reasons it was so disturbing. According to the information provided by Optus, it was a single API endpoint that was accidentally left exposed. APIs are communication tools used to let systems exchange information. They are safe when secured properly. When they are not secured, they turn into unnoticed entry points.
Incidents like this are exactly why professionals working in cyber security jobs focus so heavily on access controls, endpoint monitoring, and continuous auditing. In the current case, the attacker is said to have gained access to customer records without the need to provide authentication credentials.What is important here is not only the method used by the attacker but also, and mainly, the data that has been stored behind that particular access point. Over the years, a huge pile of personal data was gathered. Some of the data belonged to former customers who had no contract with Optus anymore.
This piece of information later became a focal point of argument.
Benefits Section Adding Value
If we talk about “advantages” related to a data breach, it sounds weird. But if we consider it from an informational perspective, there were results that changed the way data privacy is handled. One such result was the awareness that certain data practices had been conducted and the data was held for a very long time, without telecom customers even knowing. After the breach, questions started arising. Why does a telecom company still hold the personal identity documents of a customer years after the contract has ended? Situations like this pushed organizations to rethink malware protection and data security practices as part of a broader responsibility toward customer privacy.
Another result was that regulatory agencies, legislators, and companies had to reevaluate the importance of data minimization. Data kept “just in case” suddenly appeared to be a liability rather than an asset.And, finally, there was also the increased openness. It’s not perfect, but still better. Silence is no longer an acceptable response when personal data is exposed.
Real-World Examples of Impact
Some individuals were affected almost immediately. They experienced scams using their personal data, strange activities in their accounts, and a need to get new documents changing their ID.
But for the slow-developing ones, this is always the case. Everything is anxiety at a very low level and credit checks have become a routine thing. Being cautious when receiving phone calls and emails is also important.The businesses were impacted too. Optus was dealing not only with customers but also partners, regulators, and investors who were putting forward their concerns. Trust doesn’t break loudly. It erodes.By the way, the data breach turned into a reference point for other companies. Internally they started to use it as a warning example.
Common Mistakes That Made Things Worse
Not all of the biggest mistakes were those of a technical nature. One of the biggest mistakes was a communicative one.
Initial communication mostly emphasized what was not stolen thus avoiding stating the pain of the victims. No passwords. No payment details. While these facts are correct, they do not represent any kind of loss to the victim. The identity information on the other hand is something with which the victims feel vulnerable. To lose it is to lose your very self.
Another mistake was the issue of doing more with data that was at hand. It was discovered that keeping personal information for a longer period than necessary had increased the extent of the impact. It became a point of contention during the legal debate later on.Eventually, there was confusion. Customers had a hard time figuring out if they were affected and what their next steps should be. During breach situations, just as much importance has to be given to clarity as to speed of response.
Optus Data Breach vs Other Major Breaches
In comparison to some other breaches that led to the exposure of bank details, this one had a different touch. Credit card breaches cause problems, but cards can be canceled. Identity details can’t. When compared with breaches in the healthcare sector, the scale was almost the same, but the public reaction felt sharper, almost like a dagger. Now customers of telcos sit at the center of the digital world, where issues around digital identity and data security have become unavoidable, as explored in depth across broader technology and risk discussions on The Article Spot. Phones are no longer seen as simple communication devices; they’ve quietly become the primary proof of who we are.
This is the reason why the public reaction was quite strong. Disregarding the number of victims, it was almost totally about the victims’ dependence on the brand.
Optus Data Breach Privacy Lawsuit Explained
The optus data breach privacy lawsuit was initiated as a result of accusations that Optus did not adequately ensure the security of customer information (Privacy Act 1988). The plaintiffs further asserted that the company had excessively stored personal data and failed to protect it properly.Privacy laws don’t mandate companies to be flawless, rather they require companies to act reasonably. Reasonableness of the act is something that has become a key point in the debate. So, was it reasonable to keep the identity data of those who had left the company? Was it reasonable to leave the API exposed?
Those questions now sit at the heart of the case.
Optus Data Breach Class Action and Its Progress
In the class action Optus data breach, claims from millions of content customers have been aggregated. Class actions are inherently slow because they have to go through the entire discovery process, expert testimony, and have those slow procedural steps in place.Most people that take part see the case not as a dramatic compensation event, but more as an issue of recognition of their injuries, setting a certain standard, and making sure that the breach doesn’t occur again quietly and without anyone finding out.Whether that goal will be fully met remains to be seen.
Optus Data Breach Compensation: What’s Realistic

When folks hear about “compensation” their imaginations can run wild. However, the discussion regarding Optus data breach compensation is actually focused on losses that can be proven, time, stress, and ongoing risk.Some types of redress may take the form of financial payments. Others may include service credits or non-monetary remedies. Class action settlements often involve a mix of different options.What matters is proportionality. Courts look at actual harm, not hypothetical fear.
Optus Data Breach Class Action Payout: Current Outlook
The speculation about an Optus data breach class action payout continues, but the final decision has not yet been reached. Cases such as these usually take time, especially when they raise new questions about the field of digital privacy.Some people will be satisfied. Others will not. Such a situation is typical indeed. The matter of precedent is just as important as the size of the payout.
Optus Data Breach Case Study: Lessons Going Forward
This particular breach as a case study clearly depicts three aspects in which it failed.
Firstly, it demonstrates that technical simplicity does not always mean a lower risk. An exposed API can be as harmful as a highly-developed hacking attack.Secondly, data minimization should be practiced at all times. By holding less data, the future risk of harm will be reduced.Thirdly, it is just as important how those who respond to a breach sound like. People look for not just the truth, but also for compassion.These lessons have already been introduced in conversations on security that take place all over the world and not just in Australia.
FAQS (PEOPLE ASK )
When did the Optus data breach occur?
The breach was disclosed in September 2022.
How many people were affected?
Approximately 10 million current and former customers.
Was Optus fined for the breach?
Regulatory investigations are ongoing, and legal outcomes are still developing.
Can former Optus customers be part of the class action?
Yes, former customers whose data was exposed may be eligible.
Is identity theft guaranteed after a breach like this?
No, but the risk increases, which is why monitoring is advised.
Did Optus change its security practices afterward?
Optus stated it implemented additional security measures following the breach.
Can similar breaches happen again?
No system is immune, but lessons from this incident are shaping better practices.
Should consumers be more cautious with telecom providers now?
Awareness and caution are reasonable responses, especially around data sharing.
The affair hasn’t sorted itself out in some perfect conclusion. Meanwhile, the legal machinery keeps turning, rules keep getting improved, and humans keep adjusting. For many of them, it’s already part and parcel of how they perceive data. Not a big deal anymore. Just there. Quietly influencing decisions, trust, and expectations as time goes on.